STM32U585主打了数据安全,当然也提供了多种方式。我们这里用B-U585I-IOT02A开发板测试 PKA加密~也就是大家经常在计算机领域听到的公钥加密法~
我们先来看看一些导图:
应用场景:

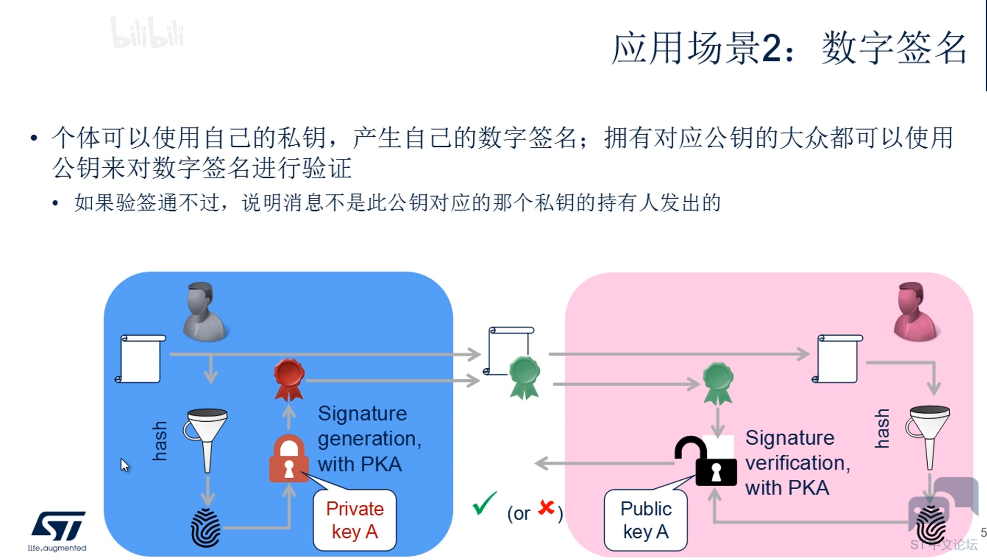
完全硬件自发,无需CPU干预:
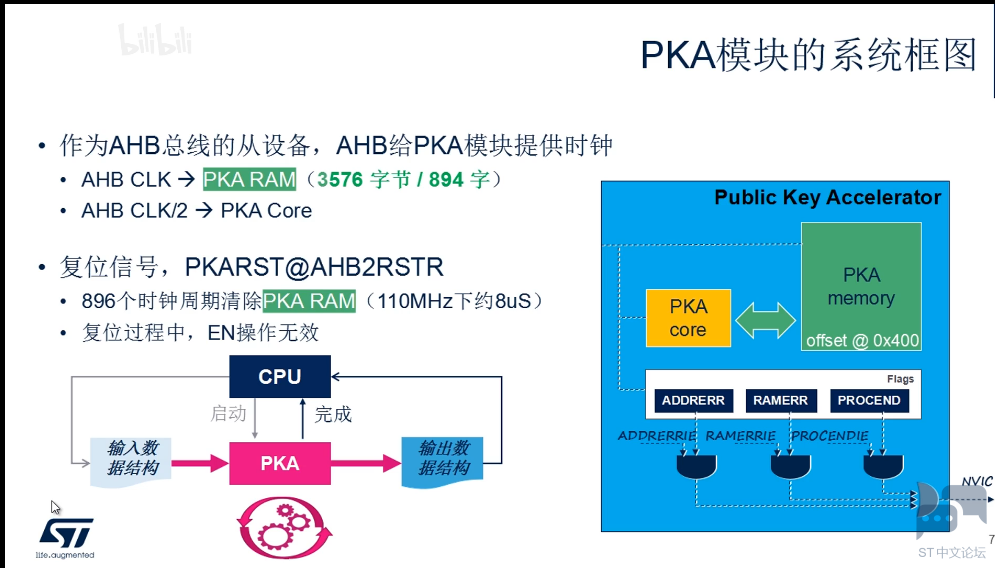
使用流程:


好,由于全在MCU内部,这了也没有什么原理图,我们直接开始CUBEMC的配置:





自动生成代码,我们添加我们的私钥及公钥对,对其进行测试:
- PKA_HandleTypeDef hpka;
- RNG_HandleTypeDef hrng;
- /* USER CODE BEGIN PV */
- PKA_ModExpProtectModeInTypeDef in = {0};
- /* Input vectors */
- uint32_t input1_OpSize = 32;
- uint32_t input1_ExpSize = 32;
- uint8_t input1_1[32] = {0xE4, 0x88, 0xD8, 0x11, 0x76, 0xE5, 0x06, 0xFA, 0xB7, 0xC2, 0xFC, 0x5D, 0xF3, 0xCB, 0x75, 0x55, 0x34, 0x3F, 0x45, 0xB4, 0x78, 0x52, 0xBA, 0x7E, 0xFB, 0xF5, 0xB1, 0x2A, 0xF4, 0x0B, 0xF4, 0xB3};
- uint8_t input1_2[32] = {0x12, 0x28, 0x49, 0x3A, 0x81, 0xFE, 0xCA, 0x62, 0x2B, 0x2D, 0x83, 0xCD, 0x97, 0x2C, 0x28, 0x23, 0x39, 0x76, 0xF1, 0xF3, 0x71, 0xCE, 0x16, 0x84, 0xA0, 0x37, 0x98, 0xE0, 0xC7, 0x0B, 0xF4, 0x39};
- uint8_t input1_3[32] = {0x45, 0xAB, 0x14, 0x95, 0x48, 0x22, 0x69, 0xC4, 0x8F, 0x1E, 0xCA, 0x23, 0x0C, 0x1F, 0x5A, 0xB4, 0xBC, 0xE7, 0x12, 0xD8, 0x50, 0x09, 0x54, 0xBB, 0xE2, 0x1D, 0x2A, 0x39, 0x86, 0x3E, 0xDB, 0xFB};
- uint8_t input1_4[32] = {0xE4, 0x88, 0xD8, 0x11, 0x76, 0xE5, 0x06, 0xFA, 0xB7, 0xC2, 0xFC, 0x5D, 0xF3, 0xCB, 0x75, 0x53, 0x50, 0x7D, 0xA2, 0xCD, 0x98, 0x24, 0x33, 0x76, 0x14, 0x8F, 0xCF, 0xA3, 0xF5, 0xCF, 0x4A, 0x88};
- uint8_t output1[32] = {0xD1, 0x2F, 0x36, 0x6C, 0x61, 0xB5, 0x66, 0x48, 0x61, 0x17, 0x8A, 0x1E, 0x6B, 0xD0, 0xE7, 0xBF, 0x66, 0x0A, 0x2B, 0x07, 0x9D, 0x4D, 0x82, 0x68, 0x7E, 0xB1, 0x9D, 0x29, 0x94, 0x43, 0x6D, 0x39};
- uint8_t buffer[32];
- __IO uint32_t hal_EndOfProcess = 0;
- __IO uint32_t hal_ErrorCallback = 0;
- static uint16_t Buffercmp(uint8_t* pBuffer1, uint8_t* pBuffer2, uint16_t BufferLength);
- /* Initialize all configured peripherals */
- MX_ICACHE_Init();
- MX_RNG_Init();
- MX_PKA_Init();
- /* USER CODE BEGIN 2 */
- /* Set input parameters */
- in.OpSize = input1_OpSize;
- in.expSize = input1_ExpSize;
- in.pMod = input1_1;
- in.pExp = input1_2;
- in.pOp1 = input1_3;
- in.pPhi = input1_4;
- /* Start PKA protected Modular exponentiation operation */
- if (HAL_PKA_ModExpProtectMode_IT(&hpka, &in) != HAL_OK)
- {
- /* HAL PKA Operation error */
- Error_Handler();
- }
- /* Wait until operation finish */
- while (!hal_EndOfProcess);
- hal_EndOfProcess = 0;
- /* Retrieve computation result */
- HAL_PKA_ModExp_GetResult(&hpka, buffer);
- /* Check retrieved result with expected result */
- if ((Buffercmp((uint8_t*)buffer, (uint8_t*)output1, 32) != 0) || (hal_ErrorCallback == 1))
- {
- /* HAL PKA Operation error */
- Error_Handler();
- }
- /**
- * @brief Process completed callback.
- * @param hpka PKA handle
- * @retval None
- */
- void HAL_PKA_OperationCpltCallback(PKA_HandleTypeDef *hpka)
- {
- hal_EndOfProcess = 1;
- }
- /**
- * @brief Error callback.
- * @param hpka PKA handle
- * @retval None
- */
- void HAL_PKA_ErrorCallback(PKA_HandleTypeDef *hpka)
- {
- hal_ErrorCallback = 1;
- }
- /**
- * @brief Compares two buffers.
- * @param pBuffer1, pBuffer2: buffers to be compared.
- * @param BufferLength: buffer's length
- * @retval 0 : pBuffer1 identical to pBuffer2
- * >0 : pBuffer1 differs from pBuffer2
- */
- static uint16_t Buffercmp(uint8_t* pBuffer1, uint8_t* pBuffer2, uint16_t BufferLength)
- {
- while (BufferLength--)
- {
- if ((*pBuffer1) != *pBuffer2)
- {
- return BufferLength;
- }
- pBuffer1++;
- pBuffer2++;
- }
- return 0;
- }
- /* USER CODE BEGIN WHILE */
- while (1)
- {
- BSP_LED_Toggle(LED7);
- HAL_Delay(400);
- /* USER CODE END WHILE */
- /* USER CODE BEGIN 3 */
- }

用PKA加密的好处就是有多种模式可选,而且不用CPU干啥,也无需外围加密芯片~s是个不错的选择!
当然,这是有大量的兑换机制有ST及其他密码学人员帮我们弄好了,其实也是挺复杂的。对于我们开
发着而言,直接拿来用即可~无需知道下单的鸡长什么~当然有大神因此去读密码学也是不是不可能~
|















 STMWoodData
回答时间:2021-10-24 21:34:32
STMWoodData
回答时间:2021-10-24 21:34:32


 微信公众号
微信公众号
 手机版
手机版
