STM32H5硬件配置有SHA1、SHA224、SHA256、SHA384、SHA512、HMAC 等更高级的运算硬件加速单元,SHA算法是常用的安全验证算法,在密码、加密等方面较为常用。如果使用单片机进行算法的演算会占用很长的机时,而且效率也较差。本次测试主要是测试SHA256的运算,同时也测试真随机数的生成和CRC16的计算加速等。 w8 b8 L9 A( |+ t
5 A: Z' N9 V& e+ A5 Q( u
% L `8 }, W0 o) F0 F( H5 r* {, J2 l# o# Q: l' S. S- B
首先 打开HASH哈希、RNG随机数生成、CRC校验等功能,程序还需要将结果通过串口输出,打开了LED1和USART3端口。 代码生成后进入printf的定义和准备测试数据。
- Q4 R+ q* L- d' r/ J$ N2 j! j- /* USER CODE BEGIN PTD */
i# |9 S: P/ | - __ALIGN_BEGIN const uint8_t aInput[] __ALIGN_END = "STM32H5 is a high-performance microcontrollers family based on Arm Cortex-M33 32-bit RISC core. It offers native and installable security services.";9 g! Z: X. D: a) I& o* o
- __ALIGN_BEGIN static uint8_t aSHA256Digest[32] __ALIGN_END;2 D; Y3 J- u* M4 R _
- __ALIGN_BEGIN static uint8_t aExpectSHA256Digest[32] __ALIGN_END = {0x02, 0xfc, 0xa4, 0x29, 0x66, 0x37, 0xc1, 0xb0, 0xc2,$ [" x; p* m( ~
- 0x8a, 0xbb, 0xe4, 0xc4, 0x15, 0x40, 0xfb, 0x8c, 0x0a,
2 S8 V% I# L* k. h - 0xb2, 0x48, 0xf1, 0xf9, 0x99, 0xa0, 0x16, 0x81, 0xd1,
4 z/ @6 @# s4 g - 0xe5, 0x1c, 0x70, 0xfe, 0x7c};; h* o' I3 b6 H+ m- x3 W
- /* USER CODE END PTD */% A6 W* L- ], p7 m5 m) R
- /* USER CODE BEGIN PV */) N0 _! Z% d8 D) v
- __IO uint32_t uwCRCValue = 0;. v, j! G; b: @
- __IO uint32_t uwRNGValue = 0;
* h( @# m' G" x# W - /* USER CODE END PV */
e# Y4 t& J! l! v) w9 ~: {准备数据时需要注意HASH算法的结果需要做对齐操作。初始化程序注意事项: / @2 F/ t. O; @
- + w" v1 Y1 Y4 Y$ e
- /**
" j' I8 Y1 N: `1 O+ E; i4 ` - * @brief CRC Initialization Function9 @' [! D5 E! ^
- * @param None6 H/ t4 ?- M$ L0 Z) _
- * @retval None7 L* {! U" C; G" H7 d0 g0 T
- */
# S; O9 `& M K$ ]7 g - static void MX_CRC_Init(void)
$ q0 w9 r2 E* l - {% \# T$ L# P1 m8 I+ @: H6 {3 m
- ( [9 e7 _- W4 @5 ]( M" s' d4 u* P$ z
- /* USER CODE BEGIN CRC_Init 0 */
. `# F) Q0 V7 T8 k- z/ T* |4 e/ ], h
& Z/ Y s" k$ v6 N) I( F6 g" z7 S- /* USER CODE END CRC_Init 0 */
- b6 z5 W) ?, q% V& u
( V! n6 e- e- g1 B8 w- /* USER CODE BEGIN CRC_Init 1 */
4 f7 v0 H/ @4 o2 O0 o b7 ]' q7 y - ; N, n n! F5 E" b8 \
- /* USER CODE END CRC_Init 1 */
" Y4 M& q, `. w" |- D: b1 P3 K- N - hcrc.Instance = CRC;
# k; J5 H: i h$ J- }$ ^4 Q" I. b - hcrc.Init.CRCLength = CRC_POLYLENGTH_16B; //as I have a 16bit polynome
4 d' W; o j( F& F - hcrc.Init.DefaultPolynomialUse = DEFAULT_POLYNOMIAL_ENABLE;
_& m3 o/ @: ^- Q+ ` - hcrc.Init.DefaultInitValueUse = DEFAULT_INIT_VALUE_ENABLE;
( X0 E P, R) e/ R7 h R - hcrc.Init.InputDataInversionMode = CRC_INPUTDATA_INVERSION_NONE;& Z6 P- l) h5 W+ r+ ~
- hcrc.Init.OutputDataInversionMode = CRC_OUTPUTDATA_INVERSION_DISABLE;4 R1 g% x; q S8 l! b# U* X
- hcrc.InputDataFormat = CRC_INPUTDATA_FORMAT_BYTES;
& z8 b. z! q# d/ [9 ^" i$ b/ q$ [5 w - if (HAL_CRC_Init(&hcrc) != HAL_OK)' ~* _5 L% o! P8 v3 v
- {
' t! ~' Y2 w6 V( s - Error_Handler();
( M2 t* C. K0 y" K J - }
- z' m8 P( b5 y, i% V: o9 A - /* USER CODE BEGIN CRC_Init 2 */
! U8 `# e: A1 N
- D0 M3 ], O2 ^1 v- /* USER CODE END CRC_Init 2 */' m6 o9 j1 K' v, b. a+ `
- 6 ^6 w% _# }" y' ?9 q; n% T
- }
9 z4 x" n) s7 J: C! r+ P' v! V
: Z; m2 y* ]" C) s2 }0 I- /**# w+ n1 M4 M# z C! j
- * @brief HASH Initialization Function2 w; ?" F% W) ]) x+ ^7 Y+ o" M/ m
- * @param None
, _" g# v. M- _8 g& S" H: o! l - * @retval None9 q9 G5 Z8 B" k Z0 I. a" y# d6 A4 l
- */static void MX_HASH_Init(void)8 P& ~1 n6 t1 l* C% J( I
- {
( `. N' {8 X/ n, G' X) n5 Z - - B j6 \! W4 S
- /* USER CODE BEGIN HASH_Init 0 */9 D9 d4 I/ _7 M" C& n$ L
. m* ?# N8 z+ @: I, g( ^* B- k- /* USER CODE END HASH_Init 0 */' B' ^6 X7 U n& A8 z
- # P- w4 u+ Q, Z. Z) r
- /* USER CODE BEGIN HASH_Init 1 */
& a8 P: ?4 l- ~3 l. x3 e - * X3 K! D* D8 H6 G5 i' D" j8 q6 d
- /* USER CODE END HASH_Init 1 */
0 }6 s- B3 X5 t. d9 C% b( @ - hhash.Instance = HASH;
6 U4 a; @' U' p+ b# \4 a a - hhash.Init.DataType = HASH_NO_SWAP;8 b$ n$ |4 }/ y" U+ n) p3 L
- hhash.Init.Algorithm = HASH_ALGOSELECTION_SHA1;
9 ~/ D6 Z3 y) S Z) x/ A - if (HAL_HASH_Init(&hhash) != HAL_OK)- q5 T1 R; M+ H* p- n, N' J
- {) N' w& z4 e( ^# r5 j* z
- Error_Handler();6 ]) ?8 {2 v' f+ q, a( U" r
- }
4 T8 D4 L' u0 f4 b# o% V! F6 Z - /* USER CODE BEGIN HASH_Init 2 */
' r1 p8 N5 ]% R2 i5 K2 k! ? - 9 B+ j9 o8 G3 S3 G8 R( F
- /* USER CODE END HASH_Init 2 */9 X3 J3 u: }8 N
- @# |0 j$ Y( ]) B$ V& ]
- }
9 `0 w: ` n1 \1 x, tHASH加速单元的设置,也是可以通过初始化来选择算法地。hhash.Init.Algorithm = HASH_ALGOSELECTION_SHA1; 定义使用何种算法,其它的可以更换。8 }: s H! t. u0 b. Z8 _
7 u u0 b* M# a9 s) N
- . K2 }$ @% I; H( F1 z2 B
- /** @defgroup HASH_Algorithm_Selection HASH algorithm selection( z9 W: s7 ]0 U% `4 k" H6 n( b; j
- * @{
& x3 L6 P3 ` m( B9 E - */8 S+ ]# _% V' O
- #define HASH_ALGOSELECTION_SHA1 0x00000000U /*!< HASH function is SHA1 */" w; i* x+ i8 m; Y) g. |) q4 }
- #define HASH_ALGOSELECTION_SHA224 HASH_CR_ALGO_1 /*!< HASH function is SHA224 */) `, u# d( Z+ w8 C3 J3 Y0 r
- #define HASH_ALGOSELECTION_SHA256 (HASH_CR_ALGO_0 | HASH_CR_ALGO_1) /*!< HASH function is SHA256 */* D5 Q8 b+ J' a) w
- #if defined (HASH_CR_ALGO_2)2 n( ~" ^; J* t* W
- #define HASH_ALGOSELECTION_SHA384 (HASH_CR_ALGO_2 | HASH_CR_ALGO_3) /*!< HASH function is SHA384 */- X0 i/ W/ D; P+ P; e4 i$ e# h
- #define HASH_ALGOSELECTION_SHA512_224 (HASH_CR_ALGO_0 | HASH_CR_ALGO_2 | HASH_CR_ALGO_3)0 L, l$ A' z1 k( Z+ \
- /*!< HASH function is SHA512_224 */
5 q* r- \! K2 |. n" |% E - #define HASH_ALGOSELECTION_SHA512_256 (HASH_CR_ALGO_1 | HASH_CR_ALGO_2 | HASH_CR_ALGO_3)
% o" X7 S0 C% o) \6 N" t( W) x - /*!< HASH function is SHA512_256 */
5 c5 }8 c6 L8 R- b/ D! n" K - #define HASH_ALGOSELECTION_SHA512 HASH_CR_ALGO /*!< HASH function is SHA512 */8 m$ g8 r, t4 Z( m1 r/ r
- #endif /* defined (HASH_CR_ALGO_2) */
y% W' ~- ^; Z- g* N/ `6 W随机数生成! z1 V t8 c* m7 p, W
W7 X# z$ p6 T0 t' G5 u- /**
8 H8 u% A; f9 S - * @brief RNG Initialization Function
- j+ T% m, P4 M4 M) V) n - * @param None" W' W6 P# R5 T5 F" s
- * @retval None! w* a3 _& i% y
- */static void MX_RNG_Init(void)0 _: x3 |4 e! P' I2 i n8 i
- {
% Q6 _3 n5 @2 Q" M s) J2 j
' f6 b+ K4 l- v% z- /* USER CODE BEGIN RNG_Init 0 */
8 Q3 ?6 _7 s# d6 m d! {7 a; x
! T' u( z" T. \' a+ W+ }% o- /* USER CODE END RNG_Init 0 */
! J) E0 c9 b, e: r2 v0 t - 6 X' E2 M9 p9 S8 p9 O/ Z
- /* USER CODE BEGIN RNG_Init 1 */
7 w; F! C+ ?- i" V6 W. ~ I - , s7 r' F! }: w$ i+ D
- /* USER CODE END RNG_Init 1 */
- \0 |3 G* c+ t9 E4 D2 B6 I - hrng.Instance = RNG;3 D% f/ @. G. Y, j( {8 Z" X1 m
- hrng.Init.ClockErrorDetection = RNG_CED_ENABLE;9 a0 Z; S4 P- Q) L
- if (HAL_RNG_Init(&hrng) != HAL_OK). P9 {! ^& s" f' ?5 _0 p0 `) u
- {
" n9 d0 S- n# e# x6 q - Error_Handler();
q9 e# {3 a4 g6 W7 M* @ - }
1 O1 h8 h/ ^: G: @4 n/ B - /* USER CODE BEGIN RNG_Init 2 */- X( J# W3 n- F7 e |# C3 o9 ~8 F! C
- : ]4 M6 }; d3 q9 Q& i3 @+ |" o3 |0 s
- /* USER CODE END RNG_Init 2 */
% Z4 s _: W3 s7 j
& S* e5 P7 ?2 I7 j- }
! C7 T' K! H& i! S6 I* W6 B+ J' Y然后是调用各功能。
4 N6 u6 g- f/ j; N6 _: [3 t+ D" Q P2 c, S
4 m0 ~# b( l1 \! K- /* USER CODE BEGIN 2 */$ @' e0 K) J1 U, c
- printf("Start a sha256!\n");" j* i5 u3 e# B" j/ S) Z1 ?# B N
- /* Start HASH computation using DMA transfer */
. v) D7 H1 a9 Z2 K2 H- l' U/ ] - if (HAL_HASH_Start(&hhash, (uint8_t*)aInput, strlen((char const*)aInput), aSHA256Digest,0xFFFF) != HAL_OK)# w+ u/ |0 z% p8 N- K5 ]3 O
- {
4 u1 G% I. w: a - Error_Handler(); J+ s! }; m- n+ c' B5 y1 ]% n4 {9 Z
- }4 P+ [# g& r7 Y* [5 p
- while (HAL_HASH_GetState(&hhash) != HAL_HASH_STATE_READY);" H/ e( L' w1 B ^- ~+ R3 J0 j! ?
- " Q% Y; y+ {: h7 w& v
- if(HAL_RNG_GenerateRandomNumber(&hrng,(uint32_t*)&uwRNGValue) != HAL_OK)! i( [8 B' B8 _+ C
- {. L7 M) [* p% J
- Error_Handler();# Z) t: E6 q$ B5 z8 g
- }: ~: L0 g( V' O7 n( u* e+ W' M/ W
- while (HAL_RNG_GetState(&hrng) != HAL_RNG_STATE_READY);
- [- n3 D! v' w B - / h/ A. n f7 G! d$ o' W3 P3 B
- printf("Gnerate Random Number:0x%X\n",uwRNGValue);
0 b" c# `* k$ f9 L) v6 A6 v! m - uwCRCValue = HAL_CRC_Calculate(&hcrc,(uint32_t*)aInput,strlen((char const*)aInput)); " T4 d1 {- H U8 q6 s
- 0 M! M$ Y9 f" U1 ^/ v
- printf("Generate CRC Value:0x%X\n",uwCRCValue);
" s* }( q G2 S. R - ! w [# ?% e$ _, x
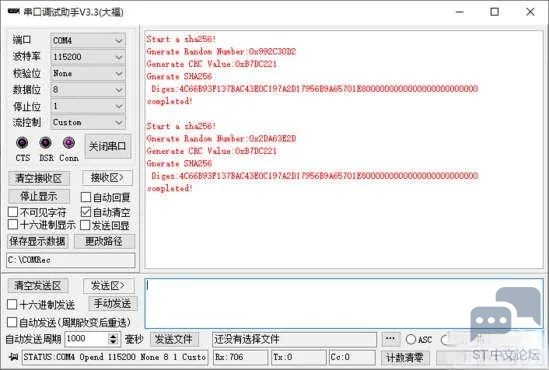
- printf("Gnerate SHA256\n Diges:");
z. E, r% K$ h+ c - for(int i=0;i<32;i++)
& u) T+ H. z' a c' Q3 F. t - {0 ~; p N6 W, M3 F3 G/ I3 j* B, w1 T
- printf("%02X",aSHA256Digest[i]);
+ \) E/ t9 m- ?0 h+ K/ c) w2 N - }% z; b2 U; l: f6 _7 W
- printf("\n");
, M2 E: S3 J9 H4 j% k' x
& e; M4 J* Y8 x+ [: C5 q, j- X" I& Q U4 B( |
. |3 E! ~/ r# q ]" X
来源:EEWORLD论坛网友 bigbat 版权归原作者所有
2 O% E: h! I/ V+ R1 U. h
0 _* C1 \+ h1 w% Z- S |



 微信公众号
微信公众号
 手机版
手机版
